Designing for Clarity in Vulnerability Reporting
Created a searchable, centralized Security Advisories hub to increase transparency, reduce confusion, and empower users to navigate security threats confidently.
Overview
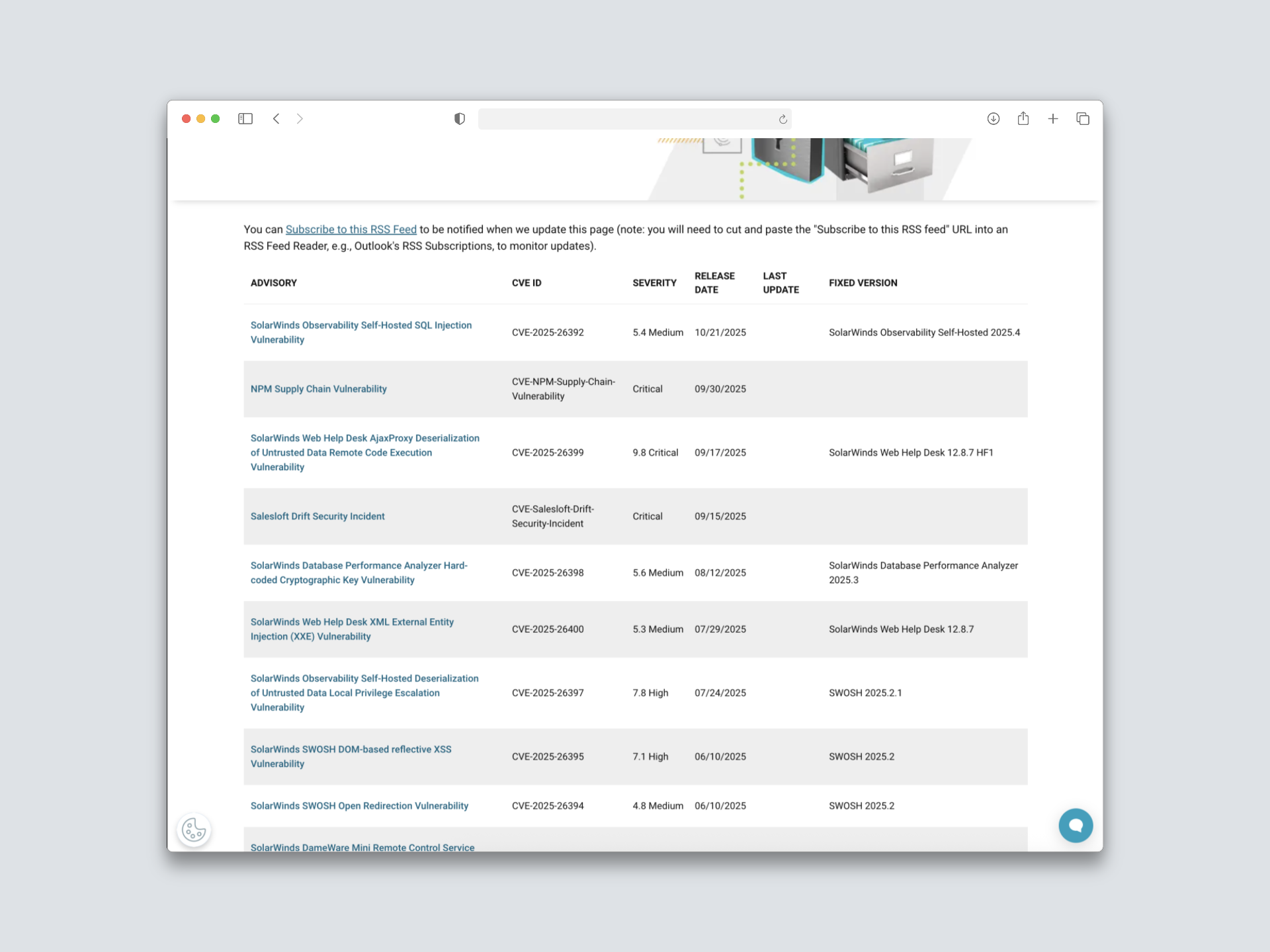
The SolarWinds Security Advisories page was originally created to publish vulnerabilities that directly affected SolarWinds products. However, customers frequently reached out to Support and Security teams with questions about third-party CVEs mentioning SolarWinds—uncertain if these impacted their systems.
To reduce confusion and improve transparency, I designed a centralized, searchable hub for all CVEs (internal and third-party). This empowered users to self-serve information and reduced unnecessary support inquiries.
“I saw on [third-party site] that this vulnerability could affect my product. Does it?”
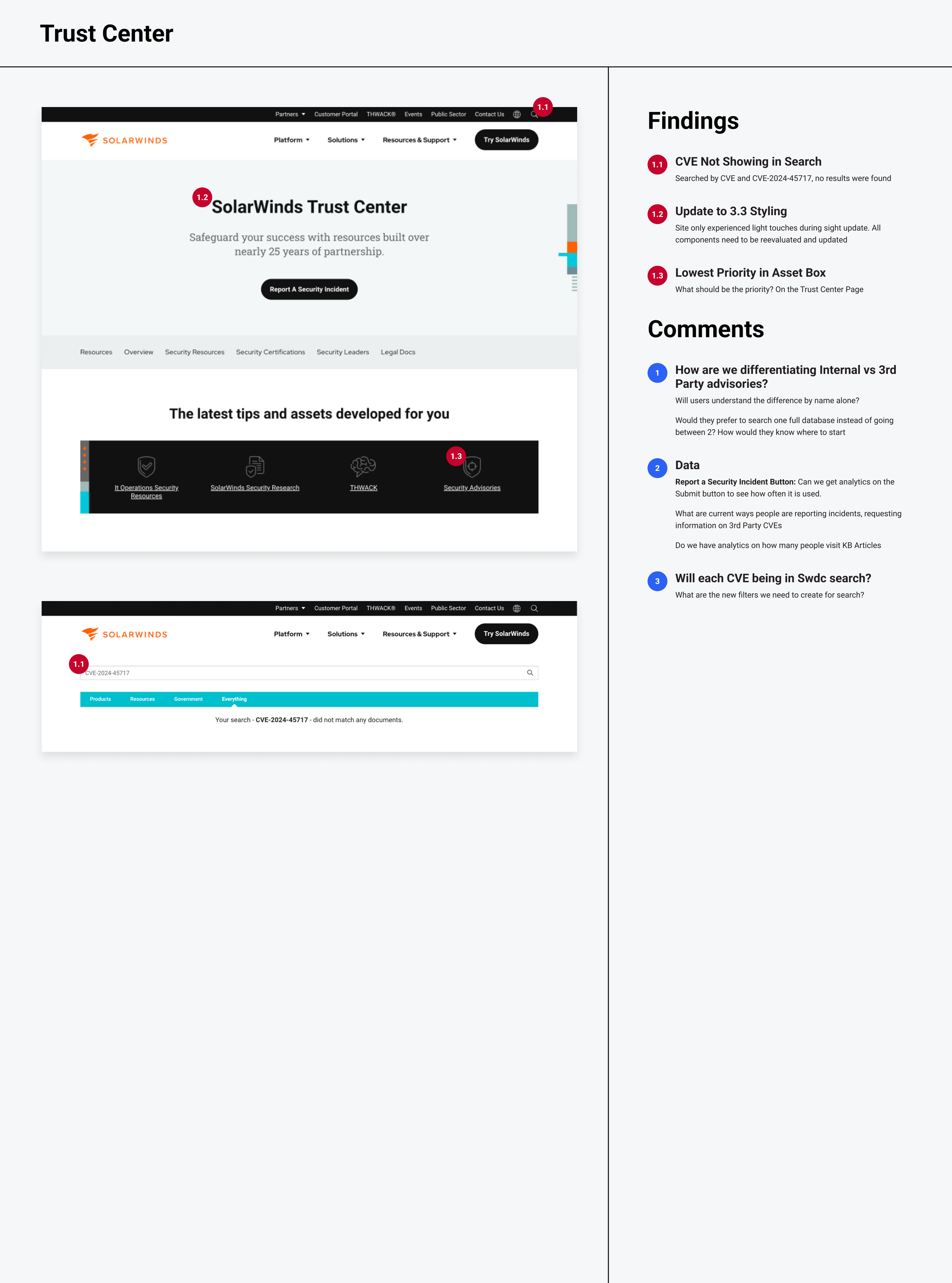
Trust Center Audit
Security Advisories Index Audit
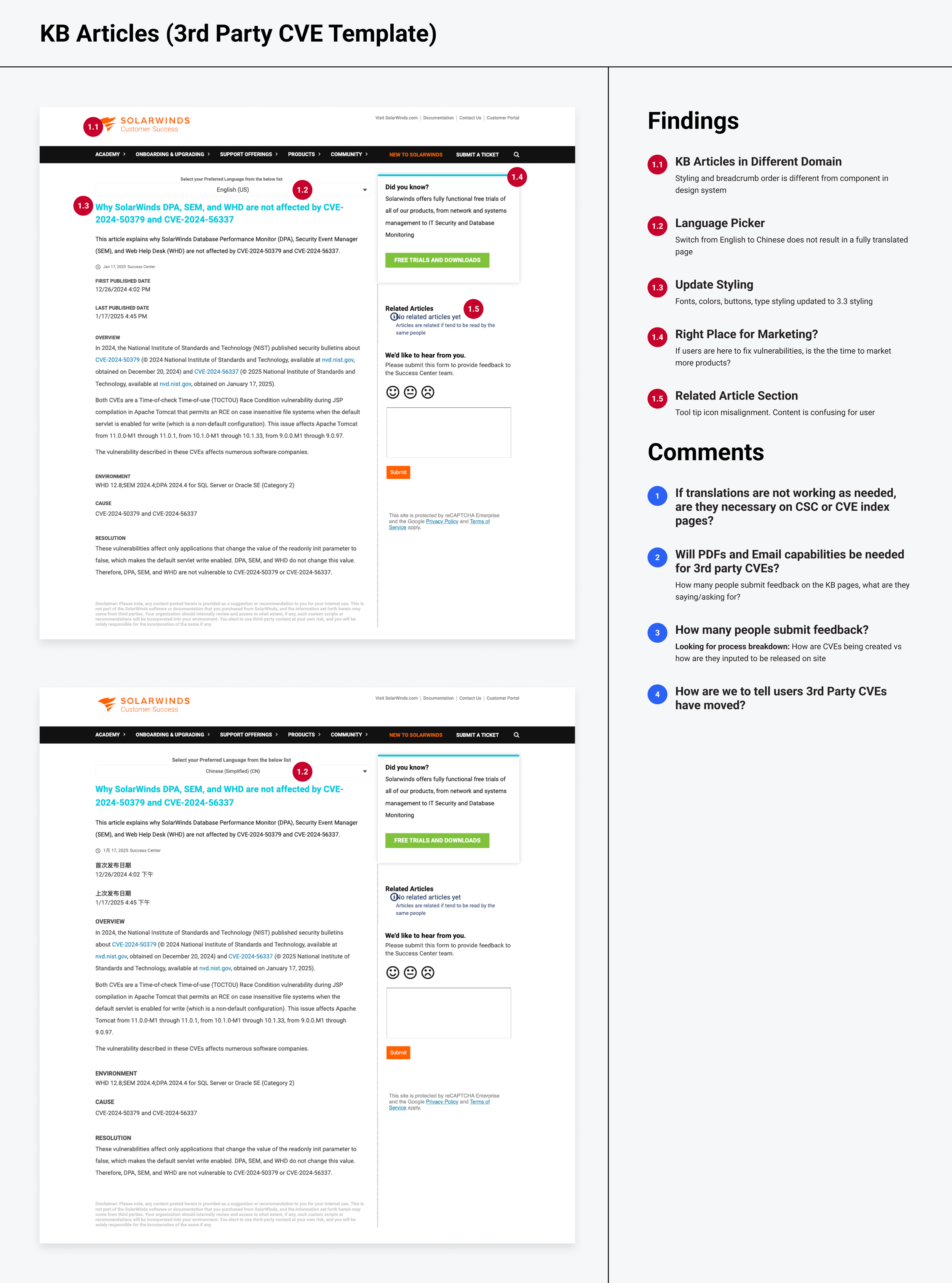
3rd Party KB Articles Audit
Security Advisories Articles Audit
The Challenge
Command F is no way to search
Technically, yes—it works. But for a table spanning six columns and dozens of entries updated several times a month, it wasn’t scalable. Users needed exact phrasing to find results, and even then, multiple hits meant scanning line by line.
Out of sight, out of mind
Third-party CVEs lived as isolated KB articles—unannounced, unsearchable, and disconnected from the main index. With no centralized database or visibility, customers didn’t even know these advisories existed. Finding them meant guessing keywords or paging through unrelated search results.
Okay… but which CVEs should I care about?
Severity scores (e.g., 5.3 vs 5.6 — both “High”) offered little real-world meaning. Users couldn’t distinguish between internal CVEs that required action and external ones that posed no risk.
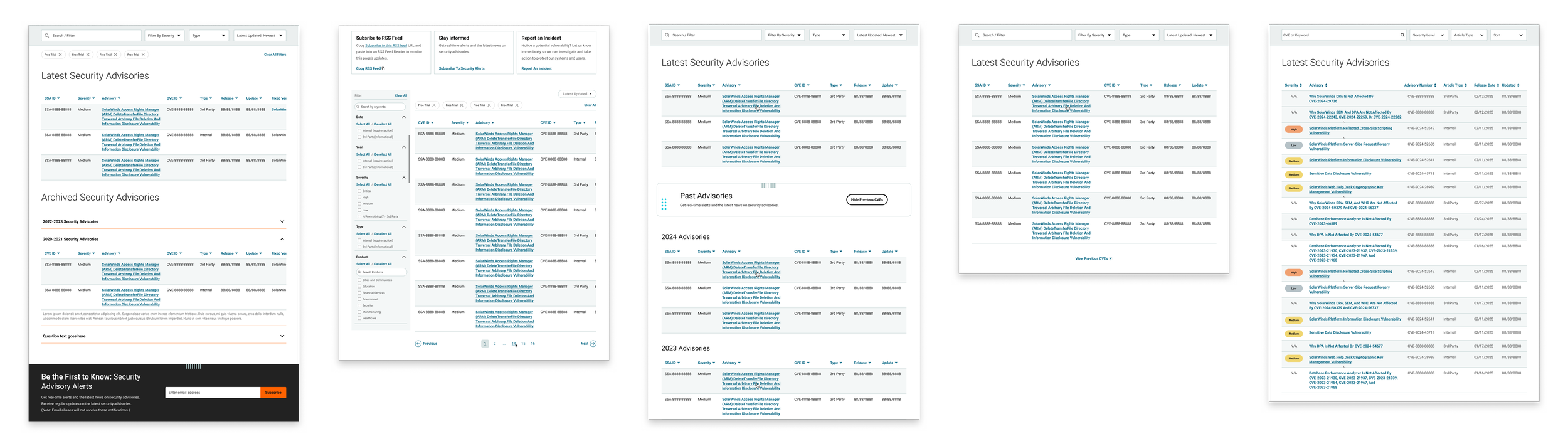
Index search iterations
Solution
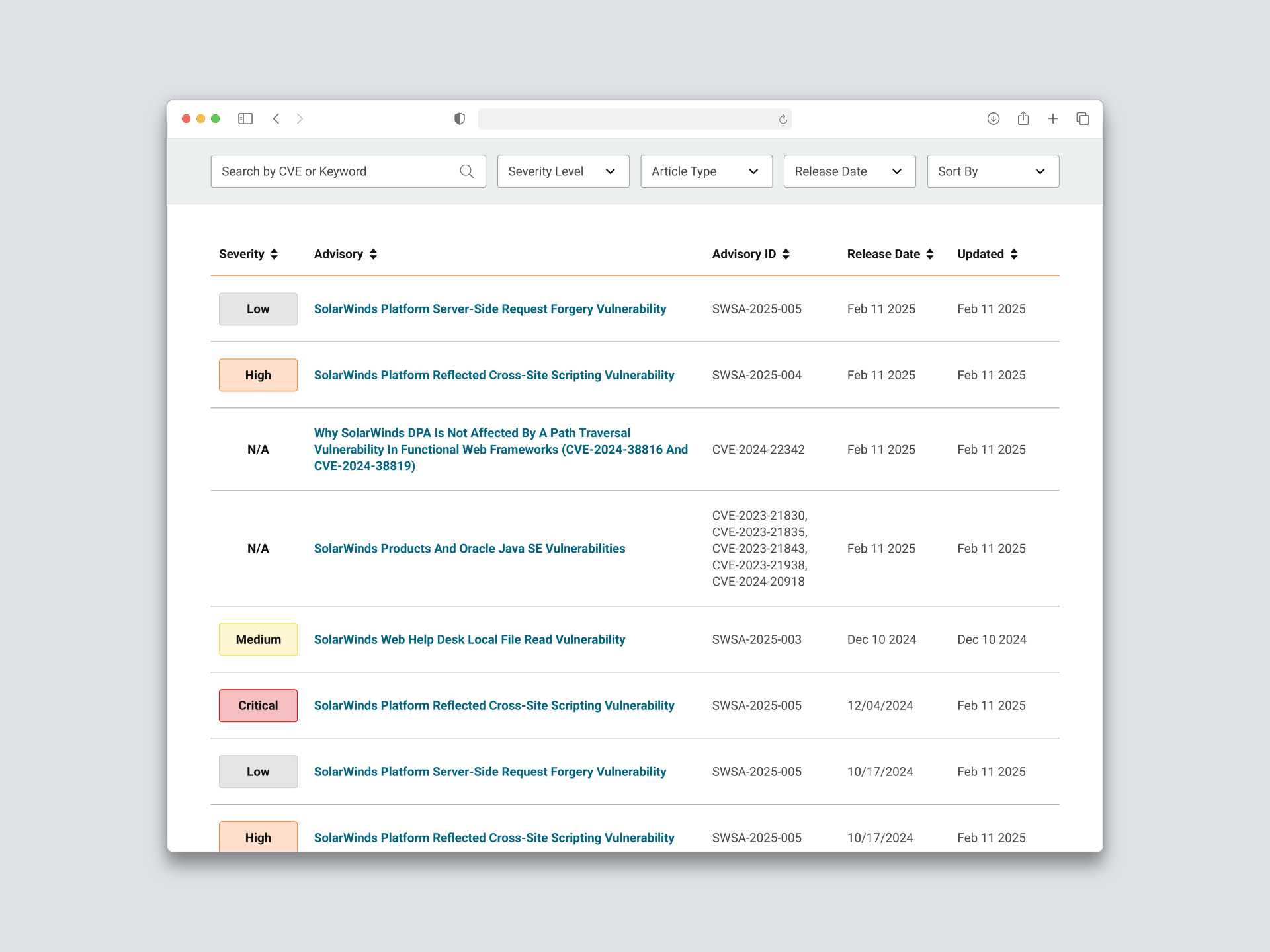
Centralized all CVEs (internal + 3rd party) in one searchable hub
Streamlined Discovery - Added horizontal filtering and sorting to help users quickly find relevant vulnerabilities by product, severity, or date.
Visual Differentiation System - Introduce clear visual cues (color, icons, and new internal “SWSA” codes) to distinguish SolarWinds advisories from third-party ones.
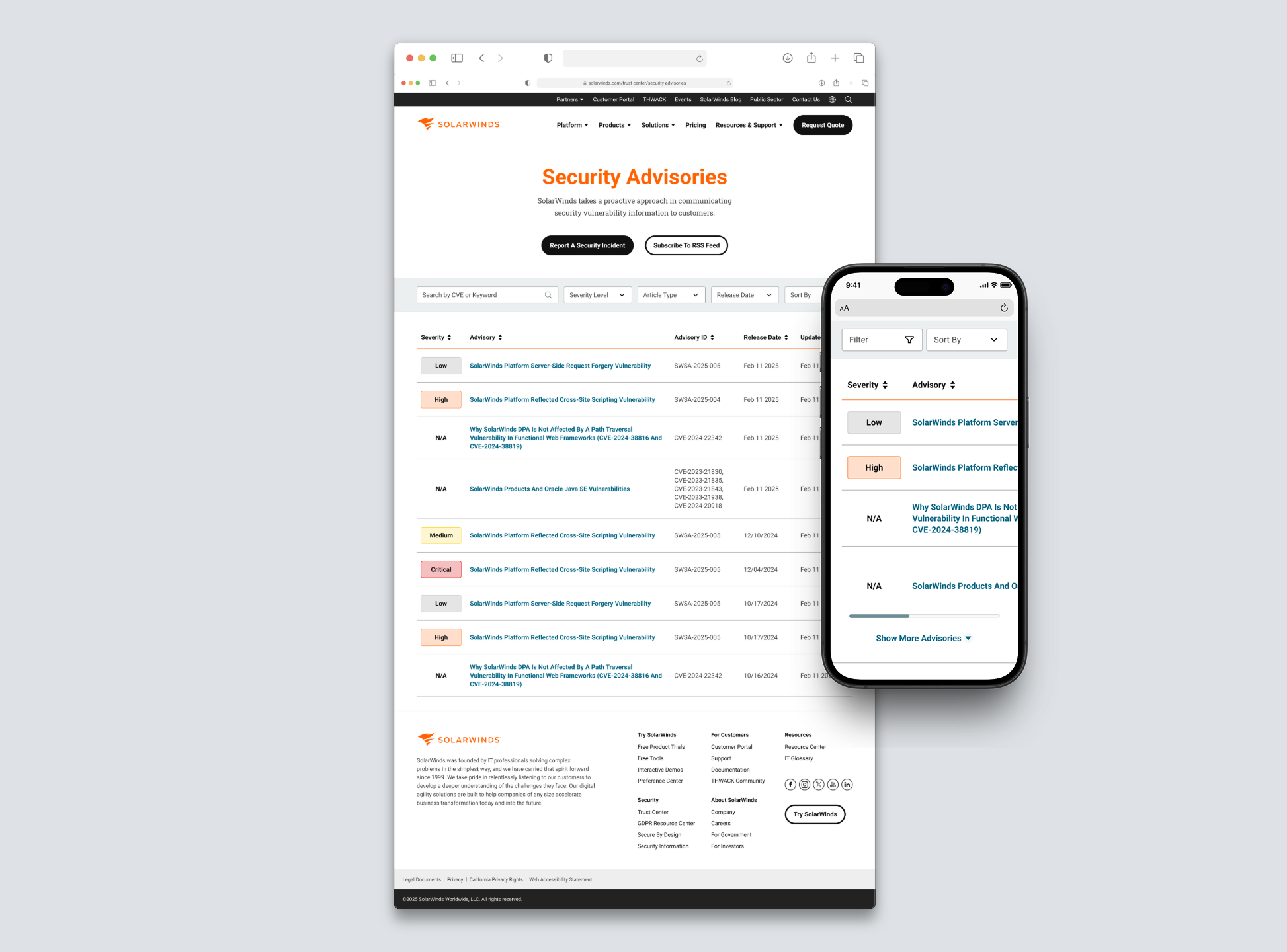
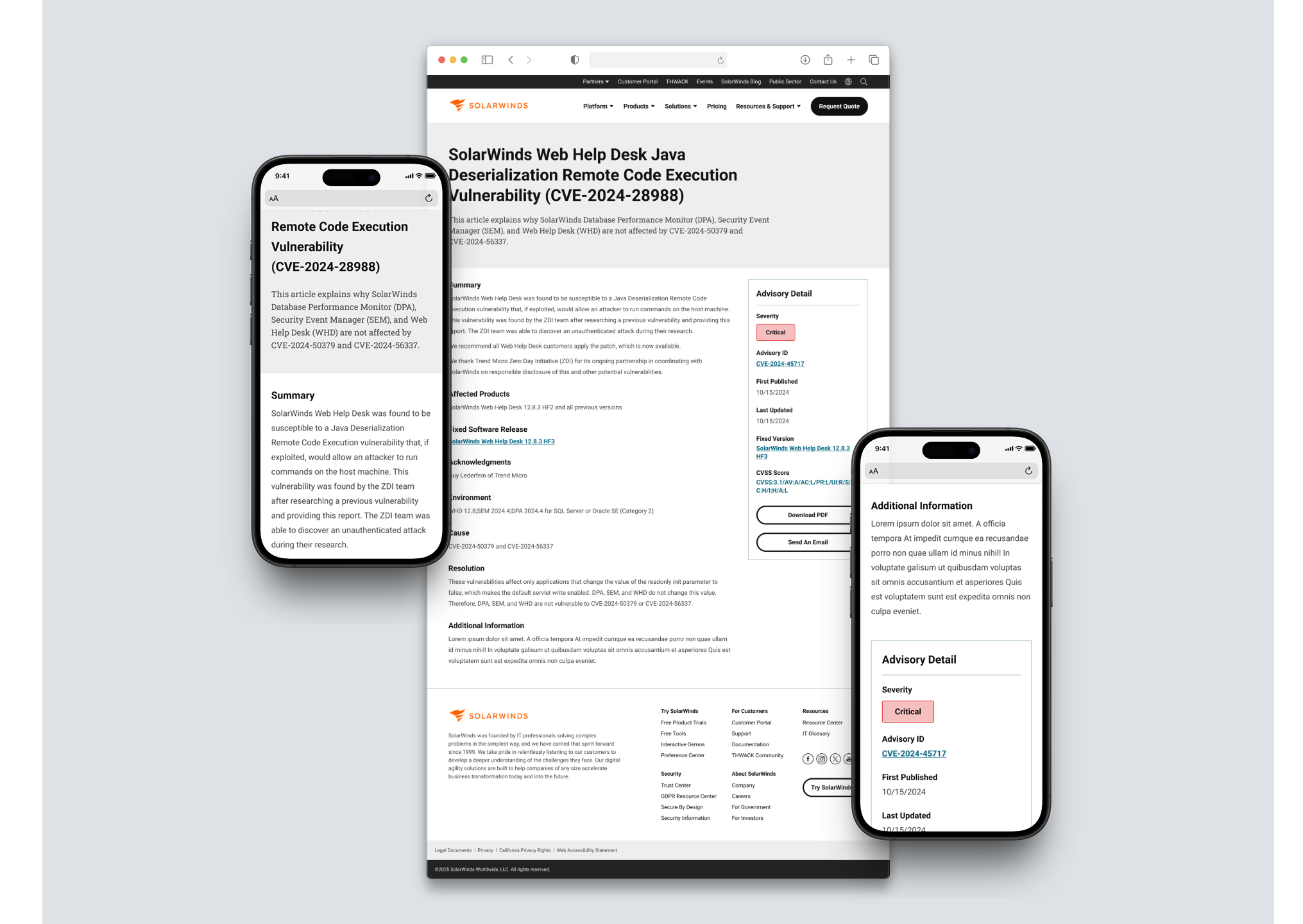
Outcome & Next Steps
The project is currently on hold pending prioritization, but upon launch, I recommended tracking the page for three months to measure:
Decrease in support cases related to 3rd-party CVE inquiries
Filter and sort usage rates
Improved findability of security information across web properties
Future Opportunities:
Cross-link advisories from product and support pages
Expand hub functionality into a searchable security database by product
Lessons Learned
Even small usability gaps (like Command+F dependency) can have major operational costs.
When it comes to security, every second counts. Customer concerned with whether or not the products they use on a daily basis are affected don’t have time to wait. Each second they are affect could be money lost. And because of that, users wanted answers quickly which resulted in our support teams getting and influx of inquiries which could have been solved with a comprehensive space for all advisories notifications. This update should result a reduction of support tickets and reports on 3rd party advisories.
Transparency isn’t just about access to data—it’s about context and clarity in how that data is presented.
A disjointed experience also can affect users getting back to normal as soon as possible. This new experience house all information in one space and allows uses to self select to get their answers quickly.